+88 0192 0098535 : info@zmintl.com





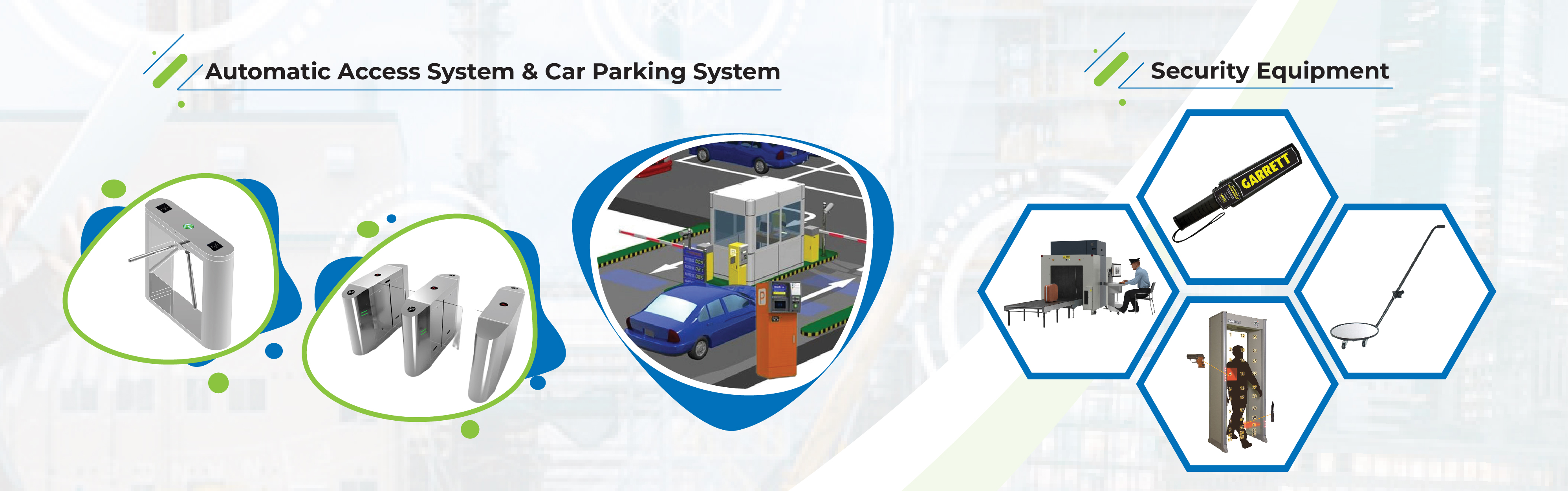










SECURITY INSPECTION
People Security Inspection Systems are critical components of security protocols designed to ensure the safety of individuals and facilities by screening people for prohibited items, contraband, or potential threats. These systems are commonly used in various settings, including airports, government buildings, event venues, and corporate offices. Here's an overview of the key components, technologies, applications, and benefits of people security inspection systems:
1. Key Components of People Security Inspection Systems
1.1. Metal Detectors
Description: Devices that detect metallic objects on a person’s body or in their belongings. They can be walk-through detectors (for scanning individuals) or handheld detectors (for more targeted inspections).
Types:
Walk-Through Metal Detectors: Typically used at entry points to scan individuals as they walk through.
Handheld Metal Detectors: Used for secondary screening of individuals identified by walk-through detectors.
1.2. X-Ray Baggage Scanners
Description: Machines that use X-ray technology to inspect bags, backpacks, and other carry-on items for concealed weapons, explosives, or prohibited items.
Features:
High-Resolution Imaging: Produces detailed images of the contents of bags, allowing security personnel to identify suspicious items.
Color-Coded Imaging: Some models provide color-coded images to help differentiate between organic and inorganic materials.
1.3. Body Scanners
Description: Advanced systems that use millimeter-wave or backscatter technology to create images of a person’s body without physical contact, detecting concealed items beneath clothing.
Applications: Often used in airports and high-security venues to enhance screening processes.
1.4. Biometric Systems
Description: Systems that use unique biological traits (such as fingerprints, facial recognition, or iris scans) for identity verification and access control.
Types:
Facial Recognition Systems: Compare captured images against a database to identify individuals.
Fingerprint Scanners: Capture and analyze fingerprints for identity verification.
1.5. Surveillance Cameras
Description: CCTV systems are often integrated into security inspection systems to monitor entry and exit points, providing video evidence of any security incidents.
Features:
High-Definition Imaging: Captures clear images for effective monitoring and identification.
Remote Monitoring: Allows security personnel to monitor multiple locations in real-time.
2. Technologies Used in Security Inspection Systems
Artificial Intelligence (AI): AI algorithms analyze data from security systems, enhancing threat detection and reducing false alarms.
Machine Learning: Systems can learn from previous data to improve accuracy in identifying potential threats.
Data Encryption: Ensures that biometric and personal data collected by security systems is securely stored and transmitted.
3. Applications of People Security Inspection Systems
Airports: Used for passenger screening, baggage inspection, and access control to secure areas.
Government Buildings: Ensures the safety of employees and visitors by screening individuals entering sensitive areas.
Event Venues: Provides security at concerts, sports events, and large gatherings by screening attendees for weapons or prohibited items.
Corporate Offices: Enhances security in high-risk environments by controlling access and screening employees and visitors.
Public Transportation Hubs: Used in train stations, bus terminals, and metro systems to screen passengers and their belongings.
4. Benefits of People Security Inspection Systems
Enhanced Safety: Helps prevent dangerous items from entering secure areas, protecting individuals and facilities.
Deterrence: The presence of security inspection systems can deter potential threats or criminal activity.
Efficiency: Streamlined screening processes help manage large crowds and maintain smooth operations, especially in high-traffic areas like airports.
Real-Time Monitoring: Provides security personnel with the ability to respond quickly to potential threats and incidents.
Data Collection: Enables the collection of data for security analysis and improvement of protocols.
5. Challenges and Considerations
Privacy Concerns: Balancing security measures with individual privacy rights is critical, especially when using biometric systems and body scanners.
Operational Costs: Initial investment and maintenance costs for advanced security technologies can be significant.
Training: Security personnel must be adequately trained to operate inspection systems effectively and respond to threats.
Conclusion
People Security Inspection Systems are essential for maintaining safety and security in various environments. At ZM International, we provide a comprehensive range of security inspection solutions tailored to meet the needs of different applications, ensuring the protection of individuals and property. Our systems integrate advanced technologies to enhance detection capabilities and streamline security processes, making them effective tools for modern security management.

| File Name | Download | Read |
| Security Screening System- (Dahua) | Download | Read |
| Automatic Access Control System- (Dahua) | Download | Read |
| Security Inspection- (Noah) | Download | Read |
| Automatic Access Control System- (Noah) | Download | Read |
| Physical Security Products- Uniqscan Catalogue | Download | Read |





