+88 0192 0098535 : info@zmintl.com















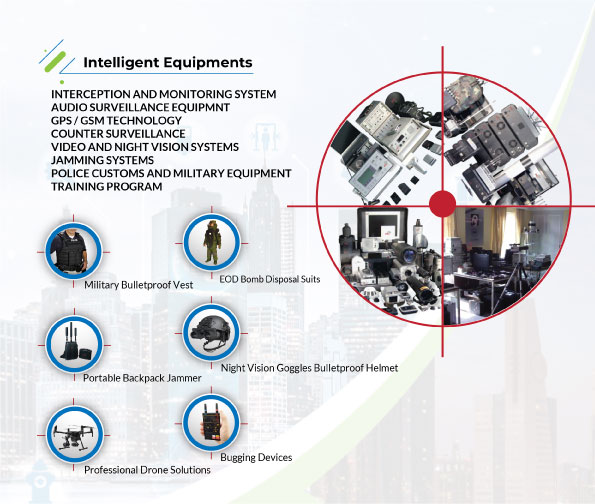
INTELLIGENT EQUIPMENTS
Anti-Terror & Intelligent Equipment focuses on leveraging advanced technology to prevent, detect, and respond to potential terrorist threats. ZM International provides state-of-the-art solutions designed to enhance security, protect lives, and mitigate risks associated with terrorism and other critical incidents. These systems integrate AI, IoT, and advanced analytics, allowing security teams and law enforcement to detect, monitor, and respond to threats in real-time.
1. Intelligent Surveillance & Monitoring Systems:
These systems use AI and advanced analytics to provide real-time threat detection and situational awareness, ensuring that security personnel can respond swiftly to potential terrorist activities.
1.1. Features:
• AI-Powered Video Analytics: Capable of analyzing live video feeds to detect suspicious behavior, unattended objects, or unusual patterns in crowded areas.
• Facial Recognition Technology: Identifies and tracks individuals of interest or those flagged in terrorist watchlists by comparing live footage with stored data.
• Behavioral Analysis: AI algorithms detect potentially threatening behaviors such as loitering, abnormal movements, or unauthorized access attempts in restricted areas.
• License Plate Recognition (LPR): Identifies and tracks vehicles that are flagged in databases, used in potential threats, or are found in suspicious circumstances.
• Crowd Density Monitoring: Automatically assesses crowd size and detects rapid increases in density, a common early warning of potential danger in public spaces.
2. Access Control & Perimeter Security:
Intelligent access control systems are crucial for securing critical infrastructure, government buildings, and high-risk areas, ensuring only authorized personnel can enter.
2.1. Features:
• Biometric Access Control: Utilizes fingerprints, facial recognition, and iris scanning to ensure only authorized personnel gain entry.
• Multi-Factor Authentication (MFA): Adds layers of security by combining biometrics with RFID cards, PIN codes, or mobile app-based authentication.
• Perimeter Intrusion Detection Systems (PIDS): Uses motion sensors, infrared cameras, and radar to detect unauthorized access to secured perimeters.
• Geo-Fencing Technology: Creates virtual boundaries around sensitive areas, triggering alerts if unauthorized devices or personnel breach the set perimeter.
• Smart Barriers & Bollards: Automatically deploy based on threat analysis, blocking vehicle access in case of a security breach.
3. Explosive & Hazardous Material Detection Systems:
Detecting explosive devices, hazardous materials, or chemical, biological, radiological, and nuclear (CBRN) threats is critical in anti-terror operations.
3.1. Features:
• Explosive Trace Detection (ETD): Devices that detect minute traces of explosives on individuals, luggage, or vehicles using advanced sensors.
• X-Ray Baggage Scanners: Advanced x-ray systems that scan luggage or parcels to identify concealed weapons, explosives, or hazardous materials.
• Chemical & Biological Sensors: Portable and fixed systems capable of identifying toxic gases, chemicals, or biological agents in real-time.
• Radiation Detection Systems: Continuously monitor for the presence of radioactive materials, triggering alarms when unsafe levels are detected.
• Mobile Bomb Jammers & Neutralizers: Disrupt and deactivate explosive devices triggered by radio frequencies or mobile signals.
4. Drone Surveillance & Counter-Drone Systems:
Drones are increasingly used in both surveillance and terrorist attacks. ZM International offers intelligent drone technology to enhance security and counter-drone systems to mitigate drone-based threats.
4.1. Features:
• Surveillance Drones: Equipped with HD cameras, thermal sensors, and AI-based analytics, these drones provide real-time aerial surveillance, enabling early detection of threats in large or hard-to-access areas.
• Counter-Drone Systems: Detect and disable rogue drones that may pose a threat to public safety or be used in terrorist attacks.
o Drone Detection Radars: Detect UAVs (Unmanned Aerial Vehicles) by identifying their radio frequencies and flight patterns.
o Jamming Technology: Disrupts the communication link between the rogue drone and its operator, neutralizing the threat.
o Laser Systems: For high-risk areas, laser-based countermeasures can physically destroy unauthorized drones.
• AI-Based Threat Analysis: Automatically assesses whether a detected drone poses a risk based on its behavior, flight path, and payload.
5. Intelligent Communication & Crisis Management Systems:
In the event of a terrorist attack or large-scale security breach, fast and efficient communication is essential to coordinate response efforts and ensure public safety.
5.1. Features:
• Emergency Mass Notification Systems: Sends real-time alerts and instructions via SMS, email, mobile apps, and public address systems during emergencies.
• Incident Command Systems (ICS): Centralized platforms that coordinate responses between multiple agencies, including police, fire services, medical teams, and government authorities.
• AI-Powered Crisis Analysis: Uses data from multiple sources (CCTV, social media, public reports) to generate real-time crisis assessments, enabling faster and more informed decision-making.
• Encrypted Communication Channels: Provides secure, encrypted communication for law enforcement and emergency response teams to ensure that critical information is shared without interception.
• Geo-Tracking and Evacuation Management: Monitors the movement of people and vehicles in real-time to coordinate evacuations and ensure the safety of individuals.
6. AI-Powered Threat Intelligence & Predictive Analytics:
Using data collected from various sources, AI-powered systems can predict potential terrorist attacks or security threats by analyzing patterns and identifying risk factors.
6.1. Features:
• Predictive Threat Analysis: AI algorithms analyze historical data, social media, and real-time intelligence feeds to identify potential terrorist activities before they happen.
• Risk Scoring: Automatically assigns risk levels to individuals, objects, or areas based on observed patterns, criminal databases, and other relevant data.
• Real-Time Data Integration: Combines data from security systems, social media, public safety networks, and law enforcement databases to provide a holistic view of potential threats.
• Sentiment Analysis: Analyzes social media trends, online forums, and other digital platforms to identify early warning signs of extremist activity or planning.
At ZM International, our Anti-Terror & Intelligent Equipment solutions are designed to enhance security and protect against evolving terrorist threats. From advanced surveillance systems and explosive detection to AI-driven crisis management tools, we offer comprehensive technologies to safeguard public spaces, critical infrastructure, and high-risk facilities.
| File Name | Download | Read |
| Intelligent Equipments- (PKI) | Download | Read |





